November 21, 2022
In its best practice manifestation, Data Governance is about being better safe than sorry. This is how you avoid falling afoul of compliance regulations such as GDPR, the HIPAA Privacy Rule, the Federal Trade Commission (FTC) Act, and many others, both internationally as well as those pertaining to the U.S. There are more coming along all the time.
Multiple other concerns, or responsibilities, need to be taken into account too when ensuring that your organization’s approach to Data Governance is best-in-class. Sound Data Governance is about not putting your organization at risk, not exposing sensitive customer or third-party information to any form of compromise, and ensuring trust in your organization.
Try though they might, however, many companies get it wrong. It’s not for lack of trying; it’s more due to a lack of deep-dive, comprehensive, holistic, and best-practice Data Governance principles across the organization.
Data Governance the Wrong Way
Many companies also get it right. Spoiler alert: if you’re one of them, skip this blog. Instead, you may want to have a quick sensitization check of how you do this by comparing your practices to NOW Privacy’s blog, ‘5 Top Tips for Data Governance and Security’’.
Getting it right has no sudden spectacular moments of proof. By definition, it’s a process of avoiding such moments, to ensure smooth and trouble-free experiences continuously arising from the smart use of your data; improving processes, accelerating workflows, informing decisions, and enhancing the customer experience.
The upside is endless. The benefits are enduring. By getting it right, an organization carries on along its success trajectory with no shocks, breaches, fines, loss of reputation, or the numerous other avoidable disasters that can arise.
It’s not necessarily true that if anything can go wrong, it will. The problem is, it might. The trick is to make sure it can’t.
If there are no rigorously developed policies and rules in place across the organization, this is where something can go wrong. If the entire organization is not on the same page about what these (ideally), openly published and readily available standards and codes of practice mean to every individual then, right there, is something that can go wrong.
Data Governance the Right Way: 3 Core Considerations
The U.S. Federal Data Strategy: Data Governance Playbook identifies six key activities of Data Governance: Identification, Management Policy, Issue Management, Assessment, Oversight, and Communications. It also states that any Data Governance policy should include: “…short statements of management intent and fundamental rules for governing the creation, acquisition, privacy, integrity, security, quality, and use of data and information”.
We have discussed the connection between Data Management and ESG success here and you may also like to check out how Data Governance influences brand perception. But for a quick pointer in the right direction for Data Governance here are the three core areas to give careful consideration to:
No. 1 – Be clear and unequivocal: Ignorance is no defense in the eyes of a Data Governance policy.
If an employee inserts one of his or her USB devices (aka Thumb-Drives) into a company computer, for example, they can unwittingly import a virus they didn’t know was on it.
If no policy explicitly forbids such mixing and matching between personally-owned and corporately-owned – or, at least, clearly and specifically sanctioned on an employee-by-employee basis – devices, the employee can hardly be blamed. The lack of detailed clarification within Data Governance policies is where such faults and erroneous behaviors originate.
No. 2 – Be alert: Cybercriminals don’t pass you by just because you have a policy.
Employees may assume that they have adhered to policy guidelines when they haven’t. It is estimated that 23.2 million cyberattack victims in 2020 were using ‘123456’ as their password. They possibly understood why a password was essential, but not that simple to them meant a wide-open door for intruders.
Making it widely known that trespassers will be prosecuted is not a deterrent to determined trespassers; impenetrable perimeters, less-than-cuddly looking guard dogs, CCTV, and armed guards are.
The more cybersecurity measures you have in place, in more places, the better protected your data is. Data Governance begins with people, is bolstered by ensuring organization-wide behaviors you expect from them to enforce your policies, and is then implemented through the third core area: technology.
No. 3 – Be smart: Cutting-edge technology cuts out outsiders.
People alone cannot solve or pre-empt the problems for you. Neither can technology alone. Putting the two together, harnessing them through powerfully developed Data Governance strategies produces a deterrent greater than the sum of its parts.
The technology has to apply to resolving any Data Governance issues present at the beginning of its creation; the clarity of education to make people aware that seamlessly harmless everyday actions can magnify into actually harmful impacts. It also has to resolve issues that may be currently inherent in how your data is managed—who has access permission, where is the data stored, are there silos of data, is there duplication, is all your data compliant, or has it lapsed out of compliance, is it clean?
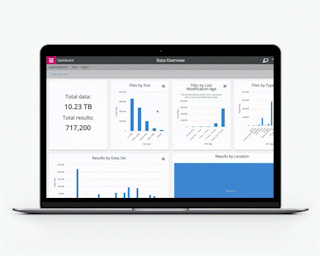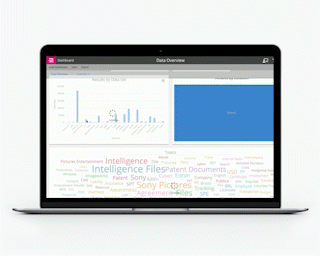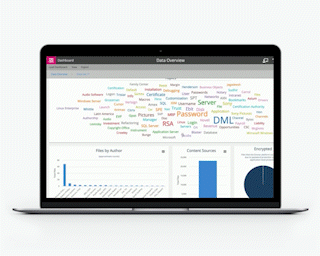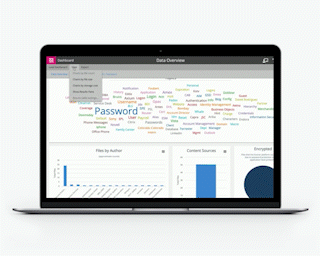
In short, the data has to be looked at as a whole, and not as a series of a constituent, possibly diverse, elements. Ultimate visibility is critical, not just from the technology perspective—but also as a reliable basis for developing appropriate Data Governance policies. It is likely that high-risk and sensitive data is hidden across your estate; deliberate use of the word “hidden.”
You need to locate all your data now. The note of urgency here is also deliberate. It is possible that outsiders are probing your perimeters, looking for a way in, or even making an exploratory perusal of your systems to see if they feel the data will be of any benefit to them. Hackers can spend weeks undetected in a system, sometimes months. They’re not usually in a hurry. Do you think perhaps you should be?
NOW Privacy can help you find true focus, on the tiniest detail, in the bigger picture of your data. This is where the problems start: in the hidden, the overlooked, and the forgotten. We can help you gain ultimate visibility of your data estate in a single location. We can do it now; because that’s the best time to do it. Find out how to uncover your risk and pump up your data governance. Now.