October 3, 2022
It’s no surprise that digital transformation has reached almost every corner of modern society. This rapid growth is changing every single aspect of how an organization stores, produces, and manipulates data.
Or at least, you’d hope so.
With this rapid growth comes various data security issues, and sometimes they appear in the most unlikely of places.
Data security is becoming such a problem that fairly tame sectors of society, like real estate agents, are looking over their shoulders. Nobody could have predicted that a decade ago. When you think about it, the real estate sector collects a vast amount of personal data.
Say, for instance, a person moving to a new town and is looking for a place to rent. First thing they would do is look at the listings on Zillow or Craigslist. Then after short-listing a few places they would speak either to the realtor or the landlord in person.
If the person in question was to go ahead, they would fill out an application, which usually involves an application fee. Instantly, the real estate company or the landlord has your credit card information. When you fill out the application form, you need to hand over some form of identification, like a driver’s license or passport.
And this is just at the application stage. Entire lives worth of data being handed to strangers in the hopes of bagging a smart 3 bed 2 bath in a trendy part of town.
If this person makes 4 or 5 applications in one town before they find a place to live, well, you see the issue here. Maybe hackers are waiting for the opportune moment, but it’s pretty obvious the next big breach will be a real estate company or landlords with large portfolios.
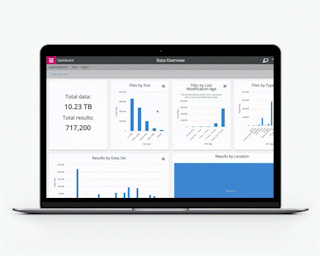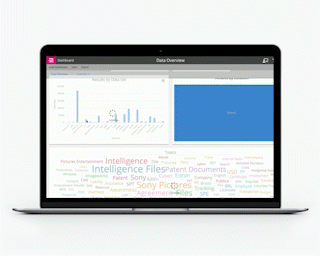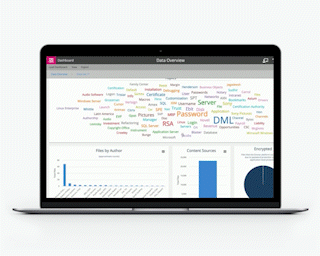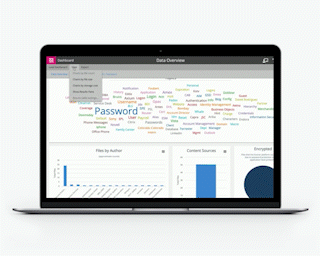
Data Breach Attack Surface Reduction
The more moving parts to an organization, the greater the attack surface. Considering that hackers have estimated they can breach 93% of company networks if they choose too, maybe even renting an apartment is now an attack vector. It’s a sad state of affairs that most organizations are simply “lucky” that hackers aren’t choosing to breach them.
Luck, as they say, isn’t a strategy.
Reducing the attack surface is now critical for any business holding personal data.
In the aftermath of Covid, it’s become really obvious to those paying attention that customers like the remote life. Ordering food, buying clothes, getting a new TV, people want to do it online. The online environment that businesses have created has grown beyond the imaginations of even the most forward looking technologist. Unfortunately, the security backing it up is still creaking along at a snail’s pace.
Or should I say, the technology is there, like NOW Privacy, it’s the culture that needs smelling salts.
A recent report by IBM suggests the average cost of a data breach is $9.44 million dollars in the United States Of America. With compromised credentials being the worst culprit, the longest breach took 327 days to identify.
That’s nearly an entire calendar year, sleeping with the doors unlocked. Imagine how many times that employee came to work, completely unaware that his/her access credentials were completely wide open. How could they stop a breach of that depth that continued for such a prolonged period?
Well, you can:
1: Take Control Of Access Your Points
Proper authentication of access credentials is by far the easiest way to gain control over your access points. Without authorization and authentication measures, there’s no way to fully understand who your data is being accessed by.
Access control squeezes that attack vector to a smaller, harder to hit surface. Hitting cyber-thieves with multiple factor authentication methods at the access point makes their job a lot harder.
2: Build Robust Endpoint Security Measures
Bulletproof endpoint security is the logical next step in securing your data assets. Simple yet effective tools can increase the efficacy of security measures tenfold.
- Firewalls between your data and the outside world
- Internal firewalls are also a possibility for extra security
- Antivirus software can also help with regular system server scans that may spot potential malware.
3: Make Encryption A Company Policy
End-to-end encryption puts yet another hurdle in the way of potential thieves. Advanced algorithms guaranteed to support initiatives like authenticity and non-repudiation.
4: Make Data Governance A Risk Assessment Policy
Risk assessment isn’t just fire extinguishers and trip hazards in the office. It also encompasses data security.
As part of a comprehensive assessment, you might ask:
- How safe are our physical assets? Could someone breach our office and go unnoticed? Do we leave access points unattended?
- How robust is our cybersecurity policy? Do we discuss this regularly in meetings?
In all actuality, depending on the size of your organization, you might need a complete overhaul of systems, processes and staff awareness training.
Stakeholders and board members constantly bring these topics to the table at luncheons or annual meetings. But the data shows that many, if not most, organizations are simply waiting to see what happens first.
Recovery measures exist if you have a massive breach and the unthinkable happens; but can you afford to have your organization shut down for days on end? In my mind, I would imagine it’s something to do with the technology itself. As a species, we love our iPhones and laptops, but only if it’s our choice to use them.
If technology is thrust upon us it can seem daunting, and yes, NOW Privacy is a sophisticated tool, but it isn’t unwieldy. Even the most tech reluctant stakeholders can grasp its potential. Data governance tools and stringent policy will be ubiquitous in the next decade, that I can assure you.
More than I know that the sun will rise tomorrow, I know that the new oil, the most valuable asset on planet earth, will be controlled and governed tighter than alcohol in the 1930’s.
Ambivalence won’t cut it when fines start hitting board members’ mailboxes. So, if it’s just an issue with tech-intimidation, don’t sweat it. All the hard work has been done. The tools exist to plug these gaps.
You don’t have to sit on the sidelines and hope you’re not 327 days from catastrophe.